From a cybersecurity perspective, the Human Machine Interface is considered the most vulnerable element in a technical system. To operate a machine, the HMI has access to all essential system data. If the system is hacked, it can have devastating consequences: operating personnel can lose control over a process, valuable data can be stolen and systems can be damaged or destroyed. In the worst case, lives can even be put at risk.
To prevent unauthorised access to the Human Machine Interface, the recommendation is to have several layers of protection. It all depends on the type of risk that would be caused by a device or machine being operated by an unauthorised person. For permanent operating points, the first step is to ensure that access to the room where the HMI is located can be monitored and controlled. This starts with a lockable door to which only authorised persons have a key and extends all the way to complex access control systems.
Securing networks
Given that many HMIs are networked today, protecting the associated network infrastructure is also crucial. This includes the wiring that connects the HMI to the network as well as measures like IP addressing, routers, switches, WLAN access points, etc. Segmenting the network using firewalls provide an additional security measure. For web-based applications, communication between the browser and the server should be secured, for example with HTTPS: the browser loads a server-side certificate and checks it for trustworthiness and validity. Based on the certificate, the data transmitted between the web server and the browser is encrypted. This way, process data and user input exchanged between the HMI browser and the HMI web server can neither be manipulated nor spied upon. Another useful security measure is to install systems that monitor network activity and can detect and ward off intruders.
Protecting the host and operating system
The operating system of the HMI itself and its hardware, such as interfaces or drives, also need protection against unauthorised access. To minimise the attack surface, unnecessary ports and system services should be disabled and unused applications removed. The operating system’s security patches and antivirus services should be kept up to date.
Authenticating the operator
Ensuring that the operator of an HMI is indeed who they claim to be is a fundamental prerequisite for ensuring security. A study conducted by Trend Micro in 2018 demonstrated the significance of secure authentication: according to the study, almost half of the successful cyber attacks on HMI systems could be attributed to insecure passwords and inadequate access rights management.
The use of passwords, as we are accustomed to from smartphones and PCs, is widespread and used for various devices. However, the protection is only as strong as the complexity of the password. Unfortunately, the use of overly simplistic passwords often comes down to work efficiency: which operator, who operates several stations within a facility, wants to or is able to enter a 16-digit password on a touchscreen keyboard every time?
Identification by badge
A solution here is badges with integrated RFID chips: as the operator approaches an HMI, the radio chip sends the identification data wirelessly to the operating terminal. This solution is particularly suitable in areas where wearing protective clothing, gloves and mouthguards is required for hygiene reasons.
Biometric methods
Biometric methods for checking access authorisation, such as fingerprint scanners integrated into the HMI, represent an even more sophisticated approach. This ensures that the respective person is actually physically present and a hacker cannot enter a command virtually.
If an HMI already works with voice control, these systems can also be used to identify the operator. Authentication via voice uses the respective voice’s individual characteristics: every single person has a unique voice with a multitude of measurable features. This voice profile is harder to fake than a fingerprint.
If an HMI uses camera systems for gesture control, it makes sense to also implement authentication via facial recognition. The biometric data of the face (for example, distance between the eyes, width of the forehead) captured by the camera is compared with a stored dataset. Modern “Face Authentication” systems are not fooled by three-dimensional masks either: the authentication process includes a genuineness check, which involves capturing the three-dimensional depth or recognising genuine skin based on a reflected infrared light beam, for instance.
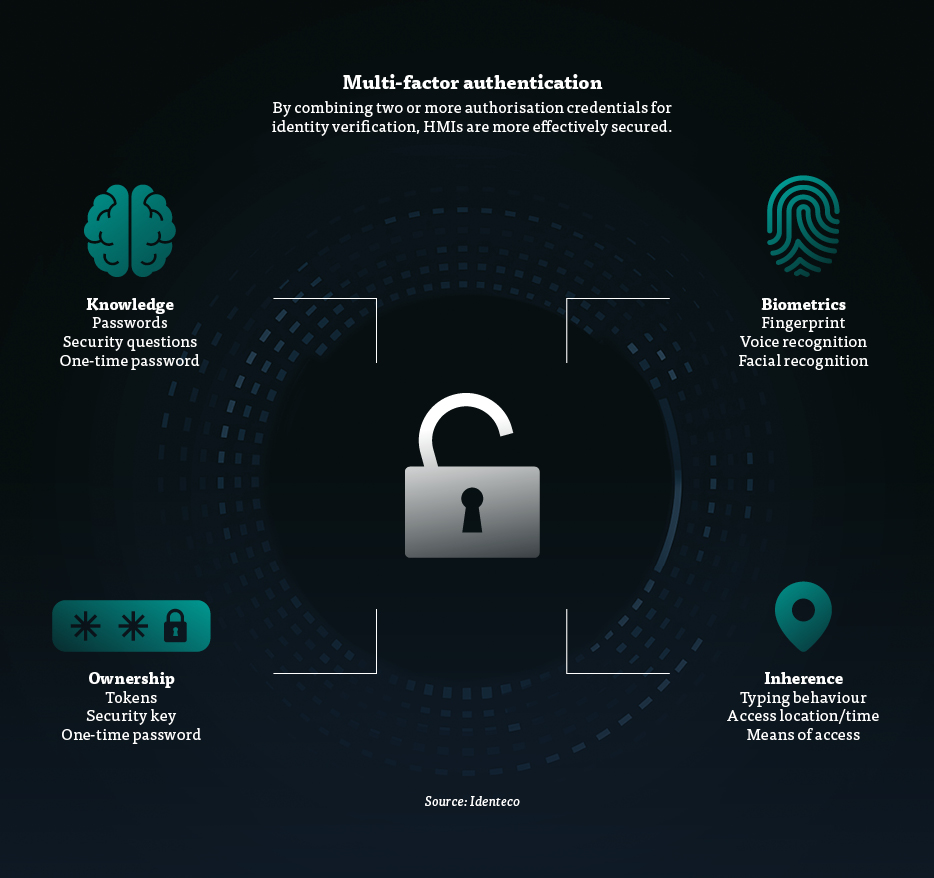
Very often, several factors are used in the authentication process, for example a fingerprint and a password. This type of multi-factor system is much more secure than using just a conventional password. While it is never possible to achieve 100-percent security in the realm of cybersecurity, combining several factors can significantly reduce the risk of unauthorised access to an HMI.