Familiar and easy to use, touchscreen displays are the public facing part of every modern-day payment system and point of sale (POS) terminal. Yet, they also have security vulnerabilities. Secure hardware and software systems that comply with the Payment Card Industry Data Security Standard (PCI DSS) are essential to building robust, protected payment products. This article looks at POS payment systems, security vulnerabilities of touchscreens and the criteria to pass PCI certification for any touchscreen.
Touchscreens in POS displays
Consumers are accustomed to paying for goods and services with credit cards on POS terminals, which feature small low-cost displays, physical buttons that match virtual buttons on the screen, and mechanical keypads to enter card numbers and PIN codes.
Today, larger colour touchscreens are replacing the mechanical buttons and monochrome displays of the past. As well as being more attractive, touchscreen displays also remove the need for moving parts, thus improving reliability.
Another trend in larger touchscreen displays is the rise of electronic cash registers (ECRs). As it is not a secure payment device, ECRs are usually combined with a POS terminal to process payments.
POS security and PCI compliance
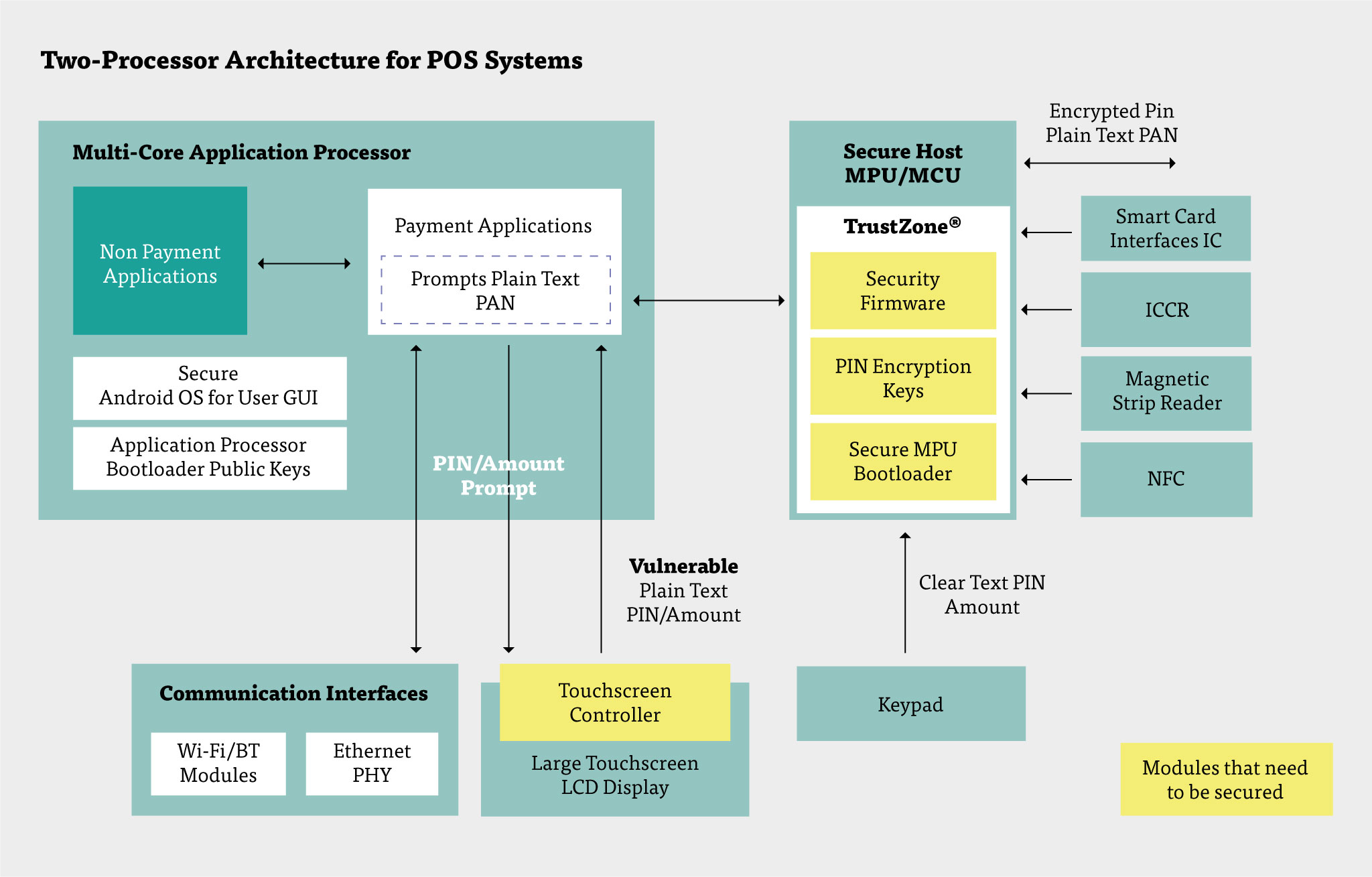
The security of user data, such as the Primary Account Number (PAN), credit card numbers and PIN, is of paramount importance. Magnetic stripe (swipe) card transactions have inherent security issues, so more secure methods include Dip (chip-and-PIN) and Tap (near-field communication: NFC).
However, touchscreens also have vulnerabilities. The transfer of touch data and PINs is vulnerable to tapping or man-in-the-middle attacks via touch sensor overlays and underlays, and even to attacks on the communication bus between the touch IC and the secure host MPU.
The touch controller firmware can be hacked to extract card details. The configuration of the touch controller can be modified to expose vulnerabilities, even on systems certified as secure.
Other security issues include extreme environmental noise, active NFC interference, extreme emissions and the need for resistance to moisture.
PCI compliance to the rescue
The major payment card brands have created the Payment Card Industry Security Standards Council (PCI SSC), which developed the PCI DSS to protect card holders’ data. Payment service providers and acceptance points have a responsibility for creating PCI-compliant products. PCI compliance requirements may change, which can affect the design of hardware, software and systems.
Most POS terminal vendors are now industry compliant with PCI Data Security Standards. If a payment system uses a separate payment module that is pre-certified to the PCI DSS for secure card transactions using a card reader with mechanical keypad, the touchscreen does not transmit any secure information via the communication lines. PCI PIN Transaction Security (PTS) certification of the touchscreen is only needed when the touchscreen is used for entering of credit card and/or PIN code data. This requires shielding the touchscreen’s communication interface or encrypting the touch message data.
General PCI certification requirements
Under PCI-PTS, PIN transaction requirements are:
- The system must shut down in the event of physical or software tampering
- Confidential user data may only be transferred when necessary (always encrypted) and stored only for as long as needed
- Conduct software updates or boot up only if software integrity can be verified
- Only authenticated users can update software
- Store key in a protected area and create mechanisms to protect key loading
- Device should self-test and report anomalies
The following features could be built into touch controller products at system level:
- 24-hourly reboot schedule
- 15-minute timeout on manual key entry
- Advanced Encryption Standard (AES) PIN encryption with ISO format 4
- Strict use of encryption keys for the intended purpose, with a separation between customer and manufacturer key hierarchies
- PAN encryption
- TR-34 Remote Key Loading (RKL) protocol
A PCI lab validates the touchscreen display to check that it meets the security requirements of the PIN Transaction Security standard. This validation includes the following tests:
- Assessing the vulnerability of the PIN entry to hacking
- Assessing access to sensitive data through tampering and examining the response mechanism
- Validation of the methods and documentation of the key management in production.
Getting to the point, quickly
Solutions such as Microchip’s maXTouch® controller portfolio can fulfil such complex system requirements. Its integrated analog front end and proprietary firmware can be configured for secure encrypted communication for any end user application.
A dedicated support team, such as Microchip Technology’s touch controller experts, can guide customers through their system level design and support them in the software/driver integration process, product testing and debugging.


